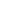Syhunt Community Edition Update 1 Released
A couple of weeks ago, on this same blog, we announced the first release of the Community Edition of our hybrid web application security scanner. Today we are making available an update for Syhunt Community that includes tweaks for Windows 10 compatibility, some bug fixes and experience improvements. Here is what is new in today's update:
- This release gives easier access to the options of scan tasks through a new menu, letting you suspend/resume a scan, view vulnerabilities, generate reports and more straight from the tasks tab:
- Tested and tweaked for Windows 10 compatibility.
- Added the ability to emulate the Microsoft Edge web browser during dynamic scans (although IE will remain for some time as the default emulation mode).
- Fixed a minor issue with the setup application (causing an elevation warning message after setup under newer Windows versions).
- Fixed a session directory creation issue when trying to code scan a directory with no valid source code files.
 |
| A screenshot of Syhunt Community running under Windows 10 Pro 64-bit. |
Download Syhunt Community 5.3.1
MD5 : 29bad37bb8cbac60d29f9f4175ae8947
SHA-1: caef9ee30d0a8ea4492efe872bf6b11ad4a68e43
Labels: Community, Free Tools, Syhunt Community Edition, Vulnerabilities, Web Application Security Scanner